On the side, I’m working on a data-breach project with a specific focus on IT-related problems. A major part of any analysis I do is separating truth from hype. And hype is a major part of the reporting done on data breaches, particularly when the breaches are due to hacking or security issues. Using HHS data on healthcare-related breaches, the hype–OMG, when hackers strike!–quickly is separated from reality–how frequent and what percentage of data breaches are hacking/IT security related. I use this as a starting point, because it allows the various parties to understand the issue at hand and develop a properly balanced risk-mitigation strategy (i.e., spend money where it counts).
At first glance, it is striking how consistent data breaches of healthcare data are (see below). One might think that data breaches are increasing, perhaps non-linearly due to reporting and how we magnify reports with our fears.
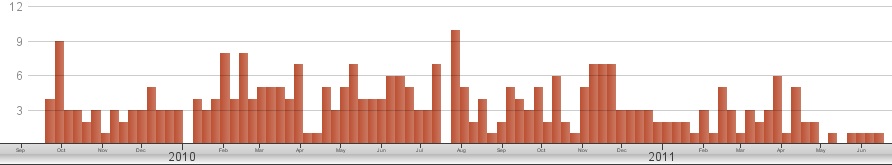
Furthermore, this consistency is found in cyber/IT/hacking-related breaches, an area where we might suspect an increasing number of incidents due to the rebirth of major hacking groups, cloud computing, and increasingly shared medical records. As the graphic below makes clear, a feared increase in cyber-related breaches is not the case.
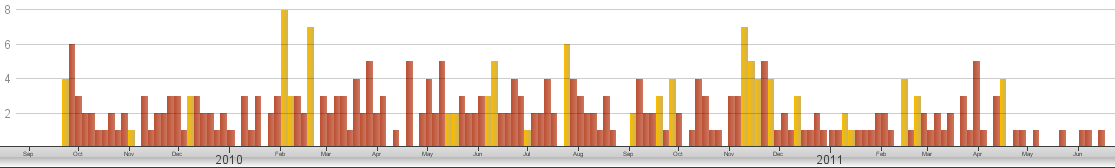
Last, if we look at the breaches by type (and, here, it is useful to have the data in front of you and manage the data to make proper analysis more insightful), we learn that improving record-handling procedures would lead to significant improvements, as it’s a combination of lost records and managing access to said records that lead to the most breaches. A more helpful analysis, which I’ve done, shows which attacks leads to the most records being breached (this is important for notification purposes and cost calculations, but not in how to prevent breaches from occurring), etc.
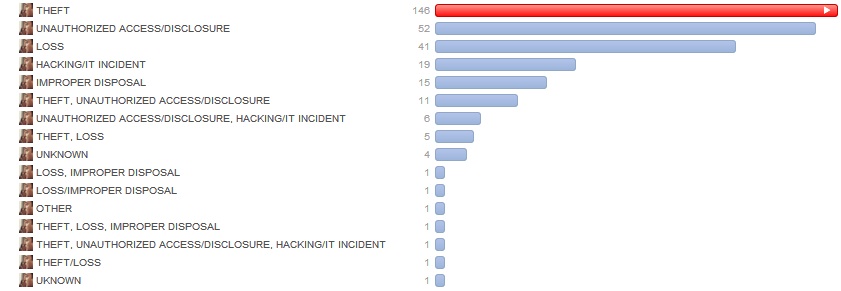
Deeper analysis of this data allows companies to properly insure data breaches, allocate rational/reasonable resources to mitigate the different types of breaches, and evolve their data handling and breach response policies over time.
A couple notes:
* Data is courtesy of HHS. This does not include unreported breaches. Due to state-reporting requirements, reporting may be biased or of varying qualities. The data could be normalized/adjusted/tweaked to provide a more clear picture, but the untouched data is useful in a few ways.
* Graphics and data handling is courtesy of Palantir Government software.
* If you or your company would like more detailed analysis, with this or other similar data, reach out to me (jasonkoepke a gmail . com).


